FlexVPN cisco对ikev2叫法 私有名称公有协议
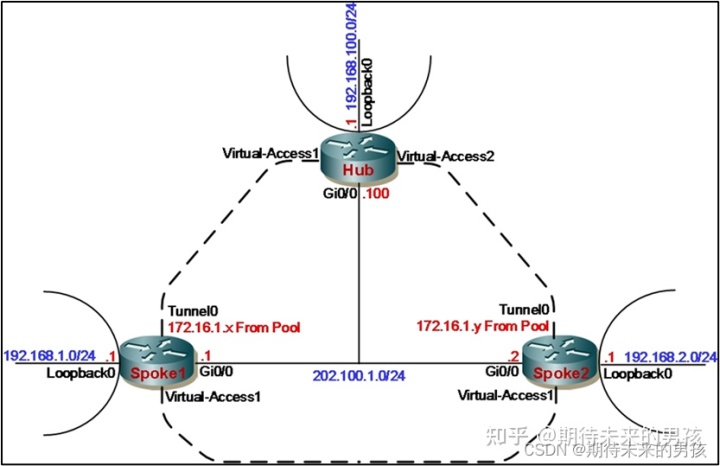
Hub
hostname Hub ! enable password cisco ! aaa new-model ! ! aaa authentication login noacs line none aaa authorization network Qytang-Author-Network-List local ! clock timezone GMT 8 0 ! ip domain name qytang.com ! crypto pki server CA database level complete no database archive issuer-name cn=HubCA.qytang.com,ou=qytang grant auto ! crypto pki trustpoint CA revocation-check crl rsakeypair CA ! crypto pki trustpoint HubCA enrollment url http://202.100.1.100:80 subject-name cn=Hub.qytang.com,ou=qytang revocation-check crl eku request server-auth client-auth ! ! ! ! crypto pki certificate map Qytang-cert-Map 10 subject-name co ou = qytang ! crypto pki certificate chain CA certificate ca 01 30820231 3082019A A0030201 02020101 300D0609 2A864886 F70D0101 04050030 2C310F30 0D060355 040B1306 71797461 6E673119 30170603 55040313 10487562 43412E71 7974616E 672E636F 6D301E17 0D313731 32323831 32343431 395A170D 32303132 32373132 34343139 5A302C31 0F300D06 0355040B 13067179 74616E67 31193017 06035504 03131048 75624341 2E717974 616E672E 636F6D30 819F300D 06092A86 4886F70D 01010105 0003818D 00308189 02818100 B7A867E0 DA6858AF 32D9264F 98B0FCA3 5BA5242B 8CA55FAD 27FEB1C6 C51A72B1 1EC40C35 8134982F 20E715B3 946333D5 705B6983 484FA71A 30798199 688A07CE 0FBBA657 5D3E9206 ED44F4FC 701ED0D2 FD06FA81 CA8B70F2 7EF5B058 F33D8EA4 C2307DE8 4D647EE0 0E06BA40 932D228F 1835EADE C5703469 026E3708 53EA91FF 02030100 01A36330 61300F06 03551D13 0101FF04 05300301 01FF300E 0603551D 0F0101FF 04040302 0186301F 0603551D 23041830 1680146C 0B32F165 9EA2A94C F68C5EDA 5B611618 C1CD5030 1D060355 1D0E0416 04146C0B 32F1659E A2A94CF6 8C5EDA5B 611618C1 CD50300D 06092A86 4886F70D 01010405 00038181 005980B5 D374D49C 6EAB7C91 25980E1E DE70EF4A C6197BE4 63C90FE8 E05AEDDE DCB8D6A7 14306DCB 4BDBBEE9 92960211 EE3E9FE0 5ED933B7 1063A0C4 046A0D8B 5F946782 E27DEB72 130B84B5 B63D3894 B302A162 54D22AA3 C8B6317A 846BFC9C CCACDD5D 77234619 C1EEBD8D E476FD15 724B018A 3156BB57 DED80C7D BD3C1A41 C6 quit crypto pki certificate chain HubCA certificate 02 30820259 308201C2 A0030201 02020102 300D0609 2A864886 F70D0101 05050030 2C310F30 0D060355 040B1306 71797461 6E673119 30170603 55040313 10487562 43412E71 7974616E 672E636F 6D301E17 0D313731 32323831 32343534 395A170D 31383132 32383132 34353439 5A304931 0F300D06 0355040B 13067179 74616E67 31173015 06035504 03130E48 75622E71 7974616E 672E636F 6D311D30 1B06092A 864886F7 0D010902 160E4875 622E7179 74616E67 2E636F6D 30819F30 0D06092A 864886F7 0D010101 05000381 8D003081 89028181 00AB9915 14E23273 9F150B0B 368FC260 B7A5EF6C 96907C81 EF1FCF66 9FCF5636 DAFBC9C0 99CB2BB5 CD0544FC 5B21748A BD640C8D 618A9383 8C991FC0 B9DBF818 ECA5BD59 EE8C9B0D E93B1EE8 3F0D8C9C 7F4E7C44 23E9BDD5 4E3B4E30 A2CB9E0B 886217C6 2CC3E06B 7D3E584A 881AA869 62F0272D DB41B2F8 6D49CE34 86E3422E 13020301 0001A36E 306C301D 0603551D 25041630 1406082B 06010505 07030106 082B0601 05050703 02300B06 03551D0F 04040302 05A0301F 0603551D 23041830 1680146C 0B32F165 9EA2A94C F68C5EDA 5B611618 C1CD5030 1D060355 1D0E0416 0414B29B C0C65E71 18999DC5 4F7EB8FD 73FEE8D9 C268300D 06092A86 4886F70D 01010505 00038181 0006A808 229F8AD5 27DC1915 460B1AB3 0D4D940A 7219BC29 20FA20C6 ADFFA32C 5FEEBFF0 5FF5D676 7D9449E0 DDF14CC7 9A8427B1 2E635291 AD729658 872098CE D6E5CB3F 4751E021 6CD60592 FE46B5B0 073A77F5 D285562F 96B84B09 8C483C05 AFB21A90 9FCD931E FE3245C8 7C6AA888 0728578D 88433903 3FA4E3BB 9C312EC8 EC quit certificate ca 01 30820231 3082019A A0030201 02020101 300D0609 2A864886 F70D0101 04050030 2C310F30 0D060355 040B1306 71797461 6E673119 30170603 55040313 10487562 43412E71 7974616E 672E636F 6D301E17 0D313731 32323831 32343431 395A170D 32303132 32373132 34343139 5A302C31 0F300D06 0355040B 13067179 74616E67 31193017 06035504 03131048 75624341 2E717974 616E672E 636F6D30 819F300D 06092A86 4886F70D 01010105 0003818D 00308189 02818100 B7A867E0 DA6858AF 32D9264F 98B0FCA3 5BA5242B 8CA55FAD 27FEB1C6 C51A72B1 1EC40C35 8134982F 20E715B3 946333D5 705B6983 484FA71A 30798199 688A07CE 0FBBA657 5D3E9206 ED44F4FC 701ED0D2 FD06FA81 CA8B70F2 7EF5B058 F33D8EA4 C2307DE8 4D647EE0 0E06BA40 932D228F 1835EADE C5703469 026E3708 53EA91FF 02030100 01A36330 61300F06 03551D13 0101FF04 05300301 01FF300E 0603551D 0F0101FF 04040302 0186301F 0603551D 23041830 1680146C 0B32F165 9EA2A94C F68C5EDA 5B611618 C1CD5030 1D060355 1D0E0416 04146C0B 32F1659E A2A94CF6 8C5EDA5B 611618C1 CD50300D 6092A86 4886F70D 01010405 00038181 005980B5 D374D49C 6EAB7C91
25980E1E DE70EF4A C6197BE4 63C90FE8 E05AEDDE DCB8D6A7 14306DCB 4BDBBEE9
92960211 EE3E9FE0 5ED933B7 1063A0C4 046A0D8B 5F946782 E27DEB72 130B84B5
B63D3894 B302A162 54D22AA3 C8B6317A 846BFC9C CCACDD5D 77234619 C1EEBD8D
E476FD15 724B018A 3156BB57 DED80C7D BD3C1A41 C6
quit
!
username ccieadmin privilege 15 password 0 Cisc0123
username admin privilege 15 password 0 Cisc0123
!
crypto ikev2 authorization policy Qytang-IKEv2-Author-Policy
pool Qytang-Address-Pool
def-domain qytang.com
route set interface
route set access-list Spoke-to-Spoke-Network
!
crypto ikev2 profile Qytang-IKEv2-Profile
match certificate Qytang-cert-Map
authentication remote rsa-sig
authentication local rsa-sig
pki trustpoint HubCA
aaa authorization group cert list Qytang-Author-Network-List Qytang-IKEv2-Author-Policy
virtual-template 1
!
crypto ipsec profile Qytang-IPSec-Profile
set ikev2-profile Qytang-IKEv2-Profile
!
interface Loopback0
ip address 192.168.100.1 255.255.255.0
!
interface GigabitEthernet1
ip address 202.100.1.100 255.255.255.0
negotiation auto
!
interface Virtual-Template1 type tunnel
ip unnumbered Loopback0
ip nhrp network-id 10
ip nhrp redirect
tunnel protection ipsec profile Qytang-IPSec-Profile
!
ip local pool Qytang-Address-Pool 172.16.1.1 172.16.1.100
ip http server
!
ip access-list standard Spoke-to-Spoke-Network
permit 192.168.0.0 0.0.255.255
!
line con 0
login authentication noacs
!
ntp masterSpoke1
hostname Spoke1
!
enable password cisco
!
aaa new-model
!
!
aaa authentication login noacs line none
aaa authorization network Qytang-Author-Network-List local
!
clock timezone GMT 8 0
!
ip domain name qytang.com
!
crypto pki trustpoint CA
enrollment url http://202.100.1.100:80
serial-number
subject-name cn=Spoke1.qytang.com,ou=qytang
revocation-check crl
!
!
!
crypto pki certificate map Qytang-cert-Map 10
subject-name co ou = qytang
!
crypto pki certificate chain CA
certificate 03
30820254 308201BD A0030201 02020103 300D0609 2A864886 F70D0101 05050030
2C310F30 0D060355 040B1306 71797461 6E673119 30170603 55040313 10487562
43412E71 7974616E 672E636F 6D301E17 0D313731 32323831 32343834 335A170D
31383132 32383132 34383433 5A306331 0F300D06 0355040B 13067179 74616E67
311A3018 06035504 03131153 706F6B65 312E7179 74616E67 2E636F6D 31343012
06035504 05130B39 584A304C 45554557 4C41301E 06092A86 4886F70D 01090216
1153706F 6B65312E 71797461 6E672E63 6F6D3081 9F300D06 092A8648 86F70D01
01010500 03818D00 30818902 818100D0 9F9421B1 D754429C B4C120B3 6C7D3BE8
6DD8D762 DB515024 C224ABDD 705F8BD0 F7807193 DE3E7071 755C8D91 D63CA7EB
309898CD B66F106C 9540E406 72A981D2 AEBE40F2 20F891D9 4817A861 EC32BD05
D86AB309 92CA6669 F93C2898 49D6E586 28CE66B1 06765F0F 7CF0BCAB 744A5024
668BFC3B 5B86C110 FB4069EF E15DFB02 03010001 A34F304D 300B0603 551D0F04
04030205 A0301F06 03551D23 04183016 80146C0B 32F1659E A2A94CF6 8C5EDA5B
611618C1 CD50301D 0603551D 0E041604 141D39DE 2D8EA167 0557E7C6 A2464BFF
6FEBA2A8 B9300D06 092A8648 86F70D01 01050500 03818100 10911C7A 6EEE16A3
6AE14C55 277D94E0 D5A0B9A3 C0396F86 0CF675D4 D0C63846 E10C9BFB EA140CE3
F61DA575 971EDC7D FB765275 18E1D613 07E63D31 74174B1E F19662BC 85295449
6E8BA553 45C3A195 4B2AF35E EB8CD7CF D283C662 2C19C8B5 6A642651 53F866F2
BA75D479 9867BED5 3EB4FC48 810CD31A F1469E9C 7C037A5D
quit
certificate ca 01
30820231 3082019A A0030201 02020101 300D0609 2A864886 F70D0101 04050030
2C310F30 0D060355 040B1306 71797461 6E673119 30170603 55040313 10487562
43412E71 7974616E 672E636F 6D301E17 0D313731 32323831 32343431 395A170D
32303132 32373132 34343139 5A302C31 0F300D06 0355040B 13067179 74616E67
31193017 06035504 03131048 75624341 2E717974 616E672E 636F6D30 819F300D
06092A86 4886F70D 01010105 0003818D 00308189 02818100 B7A867E0 DA6858AF
32D9264F 98B0FCA3 5BA5242B 8CA55FAD 27FEB1C6 C51A72B1 1EC40C35 8134982F
20E715B3 946333D5 705B6983 484FA71A 30798199 688A07CE 0FBBA657 5D3E9206
ED44F4FC 701ED0D2 FD06FA81 CA8B70F2 7EF5B058 F33D8EA4 C2307DE8 4D647EE0
0E06BA40 932D228F 1835EADE C5703469 026E3708 53EA91FF 02030100 01A36330
61300F06 03551D13 0101FF04 05300301 01FF300E 0603551D 0F0101FF 04040302
0186301F 0603551D 23041830 1680146C 0B32F165 9EA2A94C F68C5EDA 5B611618
C1CD5030 1D060355 1D0E0416 04146C0B 32F1659E A2A94CF6 8C5EDA5B 611618C1
CD50300D 06092A86 4886F70D 01010405 00038181 005980B5 D374D49C 6EAB7C91
25980E1E DE70EF4A C6197BE4 63C90FE8 E05AEDDE DCB8D6A7 14306DCB 4BDBBEE9
92960211 EE3E9FE0 5ED933B7 1063A0C4 046A0D8B 5F946782 E27DEB72 130B84B5
B63D3894 B302A162 54D22AA3 C8B6317A 846BFC9C CCACDD5D 77234619 C1EEBD8D
E476FD15 724B018A 3156BB57 DED80C7D BD3C1A41 C6
quit
!
username ccieadmin privilege 15 password 0 Cisc0123
!
crypto ikev2 authorization policy Qytang-IKEv2-Author-Policy
route set interface
route set access-list Qytang-Spoke1-Network
!
crypto ikev2 profile Qytang-IKEv2-Profile
match certificate Qytang-cert-Map
authentication remote rsa-sig
authentication local rsa-sig
pki trustpoint CA
aaa authorization group cert list Qytang-Author-Network-List Qytang-IKEv2-Author-Policy
virtual-template 1
!
crypto ipsec profile Qytang-IPSec-Profile
set ikev2-profile Qytang-IKEv2-Profile
!
interface Loopback0
ip address 192.168.1.1 255.255.255.0
!
interface Tunnel0
ip address negotiated
ip nhrp network-id 10
ip nhrp shortcut virtual-template 1
ip nhrp redirect
tunnel source GigabitEthernet1
tunnel destination 202.100.1.100
tunnel protection ipsec profile Qytang-IPSec-Profile
!
interface GigabitEthernet1
ip address 202.100.1.1 255.255.255.0
negotiation auto
!
interface Virtual-Template1 type tunnel
ip unnumbered Tunnel0
ip nhrp network-id 10
ip nhrp shortcut virtual-template 1
ip nhrp redirect
tunnel protection ipsec profile Qytang-IPSec-Profile
!
ip http server
!
ip access-list standard Qytang-Spoke1-Network
permit 192.168.1.0 0.0.0.255
!
line con 0
login authentication noacs
!
ntp server 202.100.1.100Spoke2
hostname Spoke2
!
enable password cisco
!
aaa new-model
!
!
aaa authentication login noacs line none
aaa authorization network Qytang-Author-Network-List local
!
clock timezone GMT 8 0
!
ip domain name qytang.com
!
crypto pki trustpoint CA
enrollment url http://202.100.1.100:80
serial-number
subject-name cn=Spoke2.qytang.com,ou=qytang
revocation-check crl
!
crypto pki certificate map Qytang-cert-Map 10
subject-name co ou = qytang
!
crypto pki certificate chain CA
certificate 04
30820254 308201BD A0030201 02020104 300D0609 2A864886 F70D0101 05050030
2C310F30 0D060355 040B1306 71797461 6E673119 30170603 55040313 10487562
43412E71 7974616E 672E636F 6D301E17 0D313731 32323831 32353130 355A170D
31383132 32383132 35313035 5A306331 0F300D06 0355040B 13067179 74616E67
311A3018 06035504 03131153 706F6B65 322E7179 74616E67 2E636F6D 31343012
06035504 05130B39 42335631 46444446 3537301E 06092A86 4886F70D 01090216
1153706F 6B65322E 71797461 6E672E63 6F6D3081 9F300D06 092A8648 86F70D01
01010500 03818D00 30818902 818100A3 940867B4 336B7A9A 3535E14A 42856132
163C0FDD 2819EC44 1206D9CD 4A02E891 4E5BBCEE 4D7153A8 A41E6849 DBDBF90F
FA2AB649 EBCFA3AA 25F09C1A F7AAC85F FD36005A CA807F3A BAE145D2 29EC0277
9129CE51 FCD641A1 37B35545 39336568 5E9C8D94 6729BD71 D2F48718 17BFB56D
C9C7B00D E421FF36 F85FBE0B B5B71102 03010001 A34F304D 300B0603 551D0F04
04030205 A0301F06 03551D23 04183016 80146C0B 32F1659E A2A94CF6 8C5EDA5B
611618C1 CD50301D 0603551D 0E041604 143D5FFE 6C2FFB8C BD4400E8 ED8D34DF
A31E6D86 D4300D06 092A8648 86F70D01 01050500 03818100 47DED7D2 98D4718B
DB7DBDFE 3B07A028 9469ACBF A4512185 05DEF5B7 17C59319 B751D3DB 2F980BEE
3707AC12 C627CA81 797622E1 D987A7B7 E609CB78 53B8C314 E206C773 38F25AF4
5C4E4D4F 27F3605B 61503BE2 0DCA40B0 7AABC5D1 66B89556 60D4919E 12D207A4
0DEB0DAD 84181E83 03EDC9F1 F7538911 539636C2 ED2DFCFF
quit
certificate ca 01
30820231 3082019A A0030201 02020101 300D0609 2A864886 F70D0101 04050030
2C310F30 0D060355 040B1306 71797461 6E673119 30170603 55040313 10487562
43412E71 7974616E 672E636F 6D301E17 0D313731 32323831 32343431 395A170D
32303132 32373132 34343139 5A302C31 0F300D06 0355040B 13067179 74616E67
31193017 06035504 03131048 75624341 2E717974 616E672E 636F6D30 819F300D
06092A86 4886F70D 01010105 0003818D 00308189 02818100 B7A867E0 DA6858AF
32D9264F 98B0FCA3 5BA5242B 8CA55FAD 27FEB1C6 C51A72B1 1EC40C35 8134982F
20E715B3 946333D5 705B6983 484FA71A 30798199 688A07CE 0FBBA657 5D3E9206
ED44F4FC 701ED0D2 FD06FA81 CA8B70F2 7EF5B058 F33D8EA4 C2307DE8 4D647EE0
0E06BA40 932D228F 1835EADE C5703469 026E3708 53EA91FF 02030100 01A36330
61300F06 03551D13 0101FF04 05300301 01FF300E 0603551D 0F0101FF 04040302
0186301F 0603551D 23041830 1680146C 0B32F165 9EA2A94C F68C5EDA 5B611618
C1CD5030 1D060355 1D0E0416 04146C0B 32F1659E A2A94CF6 8C5EDA5B 611618C1
CD50300D 06092A86 4886F70D 01010405 00038181 005980B5 D374D49C 6EAB7C91
25980E1E DE70EF4A C6197BE4 63C90FE8 E05AEDDE DCB8D6A7 14306DCB 4BDBBEE9
92960211 EE3E9FE0 5ED933B7 1063A0C4 046A0D8B 5F946782 E27DEB72 130B84B5
B63D3894 B302A162 54D22AA3 C8B6317A 846BFC9C CCACDD5D 77234619 C1EEBD8D
E476FD15 724B018A 3156BB57 DED80C7D BD3C1A41 C6
quit
!
username ccieadmin privilege 15 password 0 Cisc0123
!
crypto ikev2 authorization policy Qytang-IKEv2-Author-Policy
route set interface
route set access-list Qytang-Spoke2-Network
!
crypto ikev2 profile Qytang-IKEv2-Profile
match certificate Qytang-cert-Map
authentication remote rsa-sig
authentication local rsa-sig
pki trustpoint CA
aaa authorization group cert list Qytang-Author-Network-List Qytang-IKEv2-Author-Policy
virtual-template 1
!
crypto ipsec profile Qytang-IPSec-Profile
set ikev2-profile Qytang-IKEv2-Profile
!
interface Loopback0
ip address 192.168.2.1 255.255.255.0
!
interface Tunnel0
ip address negotiated
ip nhrp network-id 10
ip nhrp shortcut virtual-template 1
ip nhrp redirect
tunnel source GigabitEthernet1
tunnel destination 202.100.1.100
tunnel protection ipsec profile Qytang-IPSec-Profile
!
interface GigabitEthernet1
ip address 202.100.1.2 255.255.255.0
negotiation auto
!
interface Virtual-Template1 type tunnel
ip unnumbered Tunnel0
ip nhrp network-id 10
ip nhrp shortcut virtual-template 1
ip nhrp redirect
tunnel protection ipsec profile Qytang-IPSec-Profile
!
ip forward-protocol nd
!
ip access-list standard Qytang-Spoke2-Network
permit 192.168.2.0 0.0.0.255
!
line con 0
login authentication noacs
!
ntp server 202.100.1.100验证
HUB#sh crypto ipsec sa
interface: Virtual-Access1
Crypto map tag: Virtual-Access1-head-0, local addr 202.100.1.100
protected vrf: (none)
local ident (addr/mask/prot/port): (202.100.1.100/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (202.100.1.2/255.255.255.255/47/0)
current_peer 202.100.1.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 13, #pkts encrypt: 13, #pkts digest: 13
#pkts decaps: 12, #pkts decrypt: 12, #pkts verify: 12
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 202.100.1.100, remote crypto endpt.: 202.100.1.2
plaintext mtu 1458, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0xFEE858CD(4276639949)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x81CFFC2(136118210)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 2001, flow_id: CSR:1, sibling_flags FFFFFFFF80000008, crypto map: Virtual-Access1-head-0
sa timing: remaining key lifetime (k/sec): (4607998/3380)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xFEE858CD(4276639949)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 2002, flow_id: CSR:2, sibling_flags FFFFFFFF80000008, crypto map: Virtual-Access1-head-0
sa timing: remaining key lifetime (k/sec): (4607998/3380)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
interface: Virtual-Access2
Crypto map tag: Virtual-Access2-head-0, local addr 202.100.1.100
protected vrf: (none)
local ident (addr/mask/prot/port): (202.100.1.100/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (202.100.1.1/255.255.255.255/47/0)
current_peer 202.100.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 13, #pkts encrypt: 13, #pkts digest: 13
#pkts decaps: 12, #pkts decrypt: 12, #pkts verify: 12
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 202.100.1.100, remote crypto endpt.: 202.100.1.1
plaintext mtu 1458, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0x3689C213(914997779)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xB790FF78(3079733112)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 2003, flow_id: CSR:3, sibling_flags FFFFFFFF80000008, crypto map: Virtual-Access2-head-0
sa timing: remaining key lifetime (k/sec): (4607998/3411)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x3689C213(914997779)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 2004, flow_id: CSR:4, sibling_flags FFFFFFFF80000008, crypto map: Virtual-Access2-head-0
sa timing: remaining key lifetime (k/sec): (4607998/3411)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:排错:
有些信号IOS 认证算法不一致
确保IOS的clock在证书的有效期在里
###申请根证书##crypto pki authenticate CA
###申请个人证书##crypto pki enroll CA